Yet Another OSCP Review
I just took the OSCP Course and successfully passed the exam. There are many other great reviews of the course out there, just thought I’d add my grain of salt.
I decided to take that course as I wanted to see where I was at in terms of hacking and penetration testing skills. As some of you know, I’ve been more or less playing with code, hacks and exploits there and there for some time now. So yeah, it was time for something a little bit more formal and still hand-on.
About the PWK - OSCP lab
This training is an introductory course to penetration testing. It is not an easy certification mainly due to the time that needs to be dedicated.
The lab is composed of a simulated company network, it is well thought out. There are multiple sub-networks and dependencies between machines.
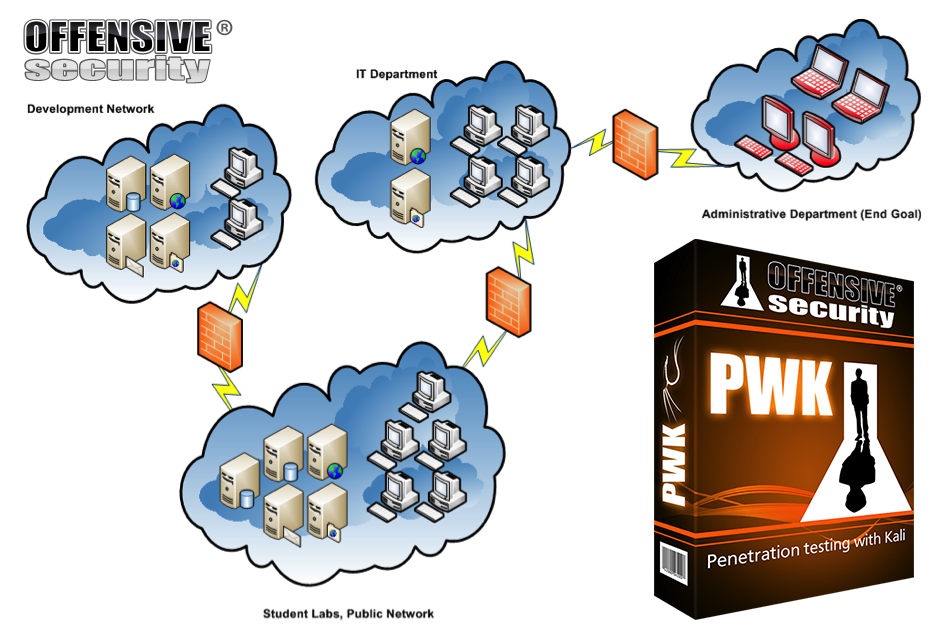
The goal is to hack and obtain administrator, SYSTEM or root privileges on as many machines as you can. You have no obligation to hack all the machines, but there are quite a lot of them which are interesting.
Machines run Linux, Windows or FreeBSD. Vulnerabilities goes from 2000 to end of 2016. You thus see a wide array of technologies, vulnerabilities and ways to hack into computers.
The course material consist of a PDF eBook and a couple of videos. Apart from that, it’s self-learning and sharing information on #offsec IRC or the forums. No information sharing about machines is tolerated though.
The staff is pretty helpful to confirm the track you’re on without giving you anything that spoil the challenges. They will help you and motivate you as long as you’ve shown that you worked hard and did the proper research.
Pre-Requisite
Many skills are recommended to have before-hand unless you want to really suffer:
- Linux and Windows command-line skills
- some basic scripting skills : some exploits modification are required in the lab
- training on vulnhub VMs will make your experience smoother and better
- IT experience : networking, development or security You could start from 0, but as some people say : they’ve suffered even though they liked the course. It is a HARD course for anyone starting in the field. But it is necessary. No way around learning the hard way and suffering a little bit.
This is NOT an exploit development course, so you don’t need to understand everything about assembly or buffer overflow or other exploitation techniques. There are buffer overflows to exploit in the course, but these are explained sufficiently in details step by step in order for anyone taking the course to understand it.
My lab run
Pwning the lab
There are 30, 60 or 90 days packages, each including an exam attempt.
I took the 30 days package as I figured I’d extend by 30 days if necessary. I ended up doing the whole lab in around 3 weeks and the remaining time for the lab report (150-300 pages depending on people). Plan time for the lab report as access to the lab is necessary for some exercises.
I started my lab around the start of February and worked on it until start of March.
I was clocking in around 10-15h/day, yeah I had the opportunity to do the OSCP lab and exam full time so I did it. In retrospect, it would have been better to take the 60 days package. It would have been a better balance.
The thing that took most of my time was recon, enumeration and post-exploitation. Some machines can’t be exploited frontally, there are dependencies between machines. Dependencies students have to find by themselves.
Taking notes while rooting boxes saved me a ton of time. I was having around 2-5 boxes a day. Fastest was 10 minutes, slowest was 5-6h. While pwning boxes, I had enumeration tools running (dirbuster, etc).
How to do it in such a limited time frame?
- have time to dedicate to the course
- be organized : exploits, notes, TTP (Tactics Techniques Procedures), etc
- run multiple scans in parallel in a staged fashion (nmap top 1000 ports then full ports while you’re analyzing the first scan, multiple dirbusters running targeting multiple machines, etc)
- statically compiled tools (if you’ve played with pivots, you probably know why ;))
- go after low hanging fruits first
- keep proper notes about every important steps you take
- do proper post-exploitation
- already have some experience
- Ask yourself the right questions. Don’t blindly follow “exploitation guides”, “penetration guides” or “privilege escalation guides”. Ask yourselves what are the objectives and goal of each steps described?
How much time should I take?
This is really subjective. I’ll based those approximations from people I spoke to on IRC. For someone with pentesting experience, been pwning quite some boxes, got time after work, I’d say 30-60 days. For someone with a good development background, got some time after work, 3-6 months. For someone with no IT skills, 1-3 years.
The most important thing being motivation and the time you can dedicate everyday to the course. This is why this certification is hard : it will take your time, you need caring people and external distractions from time to time.
Use automated scripts or not?
I typed every single commands by hand, there are multiple reasons for that:
- faster : automated scripts are great but they run scans that can be useless in the end. For instance, if you managed to find a flaw resulting in Remote Code Execution in the found web app … What use is there for running dirb, nikto, snmpwalk or SMB NULL enumeration? Once access is gained, ‘netstat’ and file enumeration are faster and better “port scanners” and “version probers”.
- automated scripts are not for speed, it is for consistency. Attack consistency can probably be fingerprinted and attack patterns be extracted.
- automated scripts are super noisy, rarely can fine tune the details
- better memorization
- better tool understanding (and thus better adaptation, not depending on a single tool)
- I can’t allow a tool to interpret data for me without me being able to check that raw data. Having interpreted data AND raw data is really important, vulnerabilities can be in the details.
Other tips?
Getting good at hacking or pentesting is not all about the technical part. Get breaks, go run, see friends, have beers, have a balanced life while doing the certification. This certification sure is addictive, so be careful.
About the OSCP exam
The exam is hard, not for technical reasons but for the duration reason in my opinion. I’ll come back to that later. If you try the exam, it means you’re kind of ready to validate your technical skills and knowledge.
The exam include 5 machines to hack. Each machines are graded from 10 to 25 points. 10 points being the easiest and 25 points the hardest. You need 70 points to pass the certification.
It is subjective, depending on your skillset, the 25 points machines may be easy for you.
The duration reason : you got 23h45 minutes to validate the exam. It looks like a long time, but hours do burn fast.
My exam run
A 0.5 box is an access obtained with low privileges. A 1 box is an access obtained with full privileges.
The duration reason is the real hard part. After some time, you also get tunnel vision and you get pretty tired. So take breaks.
Before the exam:
- a step back from hacking
- beers with friends
- going out a little bit
- some rest It helps to disconnect from the subject to avoid tunnel vision.
So what I prepared:
- a super clean and tidy room and environment
- lots of food and drinks
- breaks and naps
- No coffee, red bull or whatever substances that people use in order to stay awake. It’s a trap as you won’t be able to have efficient naps. Naps were ultra super helpful.
Attacking machine:
- a clean and fully updated and configured Kali VM
- CherryTree for note taking
- crackmapexec for popping shells (can’t use exploit/* but the multi/handler in the exam)
- metasploit multi/handler
- SecLists
- GIMP for cropping screenshots
- remmina for RDP
- bunch of other stuffs
I had 2 attempts. In both attempts, I did not use any metasploit exploits, auxiliary or post module.
1st attempt
In retrospect I could have passed with the 1st try and here are my main mistakes:
- not following my intuition : “this smells vulnerable”, almost at the end of the exam I ended up with a low privilege shell quickly on one of the box I was stucked on
- not rested enough before the exam
- too many tabs open in my browser : close them regularly
I failed for non technical reasons. Don’t take a fail as a failure but as a learning experience to further improve yourself for next time.
2nd attempt
Unfortunately, I got sick during the 48h preceding my scheduled exam time. According to Offensive Security rules, no cancelation or re-scheduling is possible during that time. So I just went on with it. I can say that it was really painful, between being tired, sick, coughing and the exam but I managed to get it.
After 4-5h + 1h (lunch) + 4-5h I had 1.5 boxes and was still poking around for recon and enumeration. I thought I was doomed. I went to sleep for 4h, waked up, got some dinner and got 2.5 boxes in 5h. I had 4 boxes, enough to pass the exam.
Stucked on the 5th box, I tried to sleep for 2-3h, but ended up reading, playing games, googling, watching “The Flash” last episode, making sure my notes and screenshots were neat, small power nap.
Went back to the 5th box, couldn’t gain access. In the end, exhausted, I stopped around 3h before the end of the exam and went to sleep.
So during those 23h45, I got around 7h of sleep splitted in 2, 15h of challenge time and 2h for entertainment and food. Refreshments during the whole exam. Those are approximates.
The next day I wrote my report and got an hypothesis as how to root the last box. This hypothesis stemed from the feeling “IT IS vuln there” I had while attempting to root the 5th box.
The next day (today), got the email with the “pass” result, it was such a relief that I could go back to a normal life again. I’ll wait some time before passing OSCE, hopefully before the end of the year.
Conclusion
Everyone would say “try harder” but not everyone knows what it means.
Try harder is the embodiment of the following:
- keep at it
- be persistent
- recon, enumerate as much as you can
- research and research more
- ask yourself the proper questions and don’t run tools blindly
- have a deep understanding of what’s happening under the hood “Try harder AND smarter.”
I mostly learned:
- be better organized for note taking, screenshots, etc
- better pivoting and file transfer tricks
- improved methodologies and intuition
It was a nerve-wrecking certification. The most nerve-wrecking part was probably before submitting the final exam report. Spent a LOT of time checking and rechecking that nothing was missed.
Anyone can do it. It is not as hard as everyone says it to be (impossible, etc). It is not an easy certification though. If you work hard, you are persistent and really keep at it, you’ll end up getting it. Don’t be discouraged by people saying it’s super hard or almost impossible to get. If you really really really want something and do something about it, then you’ll get it. You will end up having acquired hand-ons and practical skills actionable in the real world. This is not some theoretical useless certification.
In all, it was an interesting and gratifying experience. It was a really fun course if you like rooting boxes like I do.
Stay humble, work hard, be positive and keep at it :).
Good luck to anyone trying to pass that certification.